This is a sixth blog post in the series of Prevention, Detection, and Recovery from Cyberattacks.
The global survey conducted by Ponemon Institute and sponsored by IBM Security surveyed 3400 IT and IT security practitioners about their organizations’ approach to becoming resilient to security threats. The report noted that the vast majority of organizations surveyed (74%) are still reporting that their plans are either ad-hoc, applied inconsistently, or that they have no plans at all. Additionally, more than half (52%) of those with security response plans said they have never reviewed or have no set time period for reviewing or testing those plans
With business operations changing rapidly due to an increasingly remote workforce, and new attack techniques constantly being introduced, this data suggests that surveyed businesses may be relying on outdated response plans which do not reflect the current threat and business landscape.
The careful investigation of cyberattacks shows that cyberattacks can be very damaging. We have noted below a few points that will assist the organization to determine the threat actor.
Threat Actors and Attacker
Since 2010 the world has seen a significant increase in cyber-attacks across the globe. To effectively tackle these issues requires an understanding of the actors, their level of sophistication, and their determination. The figure below from the Deloitte article “Responding to cyber threats in the new reality” is a graphical illustration of Threat Actors and Attacker Determination. The figure explains the changing landscape.
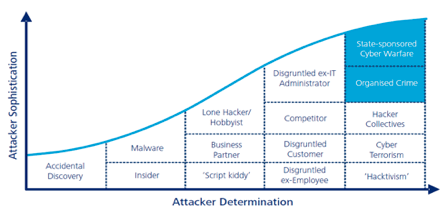
In response to the relentless threats, the industry has realized that they need to change the way they prepare, defend against, and recover from cyber-attacks.
Typical Attackers
The cyber-attacks can come from a variety of places and in a variety of forms. Some types of threats are more invasive than others, but they can all be equally jarring for a business left unprepared. A few of the typical attackers and sources of cybersecurity threats include:
- Organized crime groups
- Competitors of your business
- Hackers
- Terrorists
- Foreign governments
While the above attackers target the company from outside, another considerable threat that businesses face is inside attacks, often perpetrated by a disgruntled employee or contract worker who has been trusted with network access.
Basics
- Cyber-attacks are growing in frequency, severity, and sophistication.
- Cyber attackers exploit vulnerabilities in software, hardware, and user behavior.
- The attackers take advantage of people who fail to follow basic cyber practices and are much more likely to occur through mundane errors like:
- A user choosing an easy-to-guess password
- Using the default password on something like a router or servers
- Not changing the password frequently
- Failing to update antivirus software or patches
- Using public Wi-Fi or unprotected wireless networks
- ‘Phishing’ is also a common way to gain access to a system, this involves extracting personal information under false pretenses.
Contact contact@einnotech.com or contact@einnosec.com if you have any questions.
Visit www.einnosec.com to know more about our GRC, Audit, and Information Security practice.


